We help healthcare technology companies turn fragmented clinical, claims, and operational data into decision-grade intelligence that powers quality, risk, cost, and care outcomes in Value-Based Care models.












Customer success stories of turning inefficiencies into insights.
We trained AI models so that our client could categorize patients by Social Determinants of Health (SDoH) via Gravity Project-aligned questionnaires, integrated with EHR for actionable insights.
We partnered with a Chicago-based Health-tech client to streamline care management, enhance reporting, and strengthen compliance with chronic disease protocols through a combination of AI, automation, and modular health IT accelerators like SyncMesh.
increase in care gap closure
increase in preventive screenings

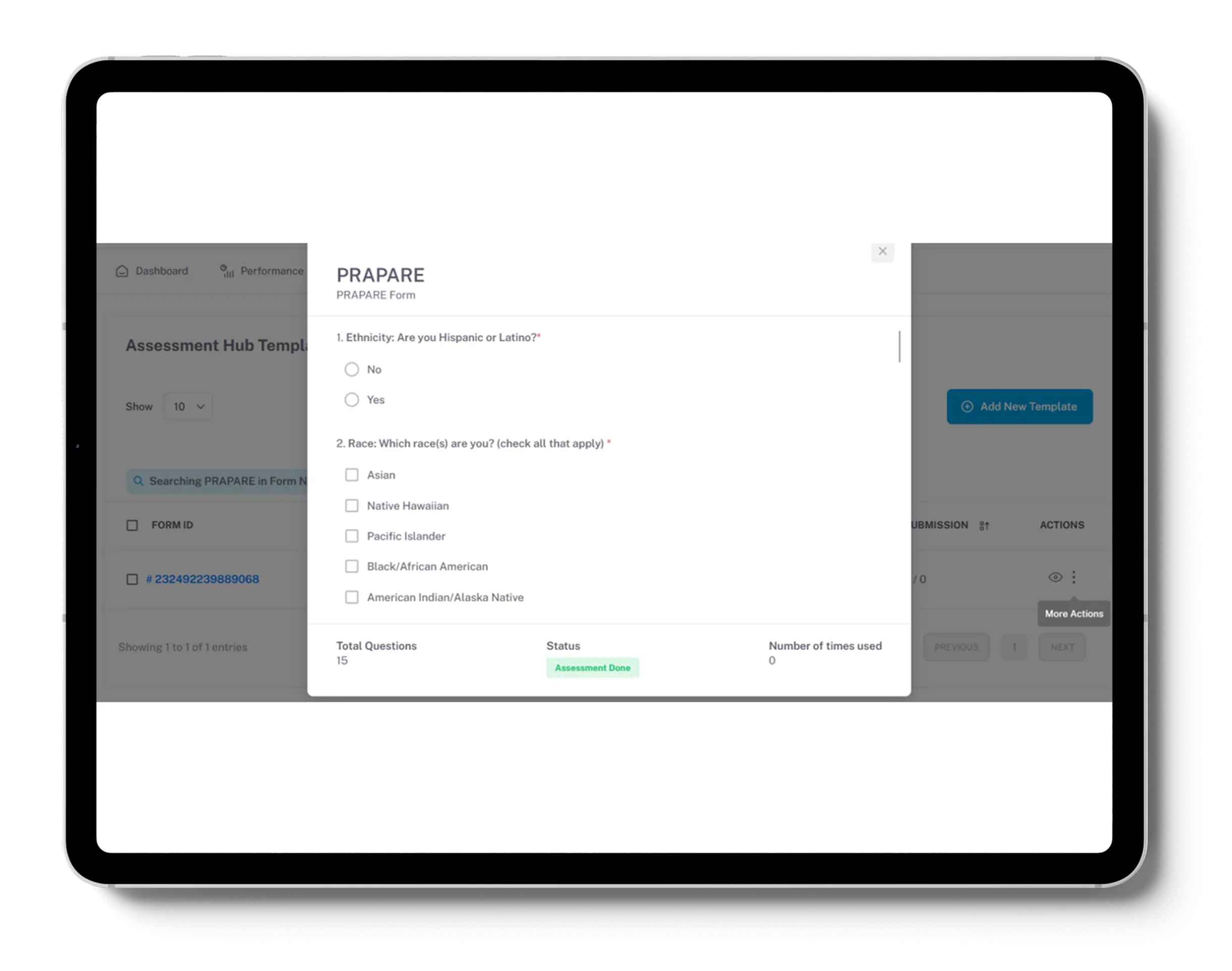
We helped US-based wound care organization serving skilled nursing facilities, assisted living centers, and home-based care networks, integrate data from PointClickCare (PCC), a leading EHR platform in the PAC segment, with its internal infrastructure, laying the foundation for longitudinal
patient visibility and analytics-driven decision-making.
replacement of manual data extraction
through fault-tolerant sync
We designed and deployed an advanced platform that integrates real-time weather data, patient vitals from IoT devices, and predictive models to mitigate heatwave risks, particularly for the elderly and chronically ill.

We designed and implemented an end-to-end Drug Diversion Surveillance & Reporting Platform—from data ingestion to real-time alerts—leveraging healthcare domain expertise, advanced AI models, and secure, modular architecture.

We designed and deployed a national-grade SNOMED CT Terminology Server infrastructure, integrating Snowstorm with HAPI FHIR and enabling a North American nation’s healthcare providers to share accurate, consistent, and standards-based clinical data across the continuum of care.
reduction in coding errors

We designed and developed a Collaboration Platform — a cloud-native, HIPAA-compliant, multi-tenant collaboration platform tailored for healthcare roles.

HIPAA Compliant
Sprint Model
Seasoned engineers, analysts, and product experts with hands-on US healthcare delivery experience.
Expert developers in building data foundations that power quality measurement, risk stratification, and longitudinal patient views.
Specialist engineers in predictive models that support risk adjustment, gap identification, and VBC performance insights.
Deep hands-on expertise in FHIR, HL7, HEDIS/eCQMs and CMS reporting standards to ensure data quality and compliance.
Proven practitioners in real-world EHR, claims, and operational data integration, powering longitudinal records that VBC platforms depend on.
Domain specialists in driving HEDIS, Stars, and custom VBC metric pipelines that consistently produce trustable results.
Expertise in automating clinical and care coordination tasks linked to measurable quality, cost, and outcomes improvements.
A little more about what drives us, how we work, and why we do what we do.
TechVariable helps US healthcare teams enable interoperability, data foundations, and analytics workflows for Value-Based Care use-cases.
Our work typically includes integrating clinical and claims data, normalizing it using healthcare standards, and enabling downstream analytics and workflows for care gaps, quality measures, care coordination, risk stratification, and CMS-aligned programs.
We work best with:
• Healthcare technology and product companies
• Value-Based Care enablement platforms
• Analytics and data platforms operating in healthcare
• Organizations supporting CMS-aligned or VBC programs
If your product or service depends on trusted clinical and claims data, we are usually a strong fit.
Our primary focus is US healthcare.
Our domain expertise, delivery practices, and frameworks are built specifically for healthcare interoperability, data engineering, and regulated environments.
No.
We are a technology enablement and services partner.
We do not sell a packaged platform. We work with your team to design and implement the data, interoperability, analytics, and workflow capabilities needed for your specific use-case.
Interoperability enablement means making healthcare data usable and trustworthy across systems, not just moving data from point A to point B.
In practice, this includes:
• Integrating data across EHRs, claims systems, and operational tools
• Normalizing data using standards like FHIR, HL7v2, CDA, and terminologies
• Preparing analytics-ready datasets for downstream workflows and reporting
Interoperability is the foundation that enables Value-Based Care use-cases to function reliably.
Most engagements start with a short discovery phase to align on:
• Data sources and standards in scope
• Target use-cases and workflows
• Constraints, risks, and success criteria
From there, we propose an execution plan with clear milestones, sprint cadence, and delivery ownership.
We provide an initial range based on scope and complexity, then refine it after discovery.
Healthcare integrations often vary widely based on data quality, system constraints, and standards implementation. We plan and price with explicit assumptions to avoid surprises later.
We typically work in two models:
• Dedicated Pod Model
A cross-functional team delivering on a sprint cadence.
• Fixed Scope / Fixed Price
Used when requirements and acceptance criteria are clearly defined.
We’ll recommend the model that best fits the use-case and delivery risk.
Yes.
We can assess your current architecture, codebase, data pipelines, and integrations, then propose a stabilization and recovery plan. Our initial focus is restoring reliability, observability, and trust before expanding scope.
“Done” means the system is operationally reliable, not just deployed.
That typically includes:
• Predictable data pipelines
• Normalized and governed datasets
• Traceable logic and outputs
• Downstream teams able to use the system without constant manual reconciliation
Explore expert videos, podcasts, blogs, and whitepapers designed to help healthcare leaders stay ahead of industry trends and innovations.






GUEST -
Keith Deutsch

GUEST -
Peter Preziosi