Understanding HIPAA-Compliance AWS Architecture
People are becoming more and more aware of their rights and privacy as a result of the tremendous shift to digitizing personal information. Healthcare organizations are required by law to ensure that their systems and procedures for handling Protected Health Information (PHI) properly adhere to HIPAA rules.
What is HIPAA Compliance?
We all have digital copies of our medical histories. We have records of all of our doctor visits, as well as records of every test we’ve had and every one of the outcomes. These documents are exceedingly confidential to a patient, and the information they contain is quite sensitive.
HIPAA enters the picture to secure this data. The Health Insurance Portability and Accountability Act is referred to as HIPAA. This law guarantees the privacy and protection of sensitive data, and when it comes to storing this kind of sensitive data on the cloud, AWS is one of the greatest options available.
Understanding HIPAA Compliance - The Breakdown
Our primary asset is an AWS account. The infrastructure of the healthcare organization can be built upon the highly secure and scalable AWS cloud. AWS offers a number of services to construct an application stack that is highly available, scalable, and secure and can support an infinite number of healthcare apps and use cases.
The physical layer, the network layer, and the data layer are the three main layers that make up the AWS Cloud
The real data centers where the servers and the entire infrastructure are housed are referred to as the physical layer. When we discuss something in the cloud, that thing should have a physical presence, and those physical presences are the data centers. AWS gives the security in these data centers the utmost consideration.
For instance AWS limits access to data. They have stern access regulations and extensive surveillance to monitor who accesses the data centers. The network layer follows, where AWS employs cutting-edge security measures to safeguard data transfer.
For illustration, suppose there are two sources, A and B. Between these two sources, the information this patient requires is transmitted. Therefore, the sent data is extremely vulnerable to attacks when it is traveling.
AWS therefore employs a variety of procedures, including encryption, in which data is encrypted during transmission and can only be unencrypted at the source. AWS employs a variety of encryption methods, making it nearly impossible for someone, such as a hacker, to obtain and decrypt the data. That is the destination Source.
The data layer comes after that. The real patient data is listed or kept in this location. Data encryption is one of the capabilities offered by AWS’s HIPAA-compliant architecture, which ensures data security even when it is being held on the service.
Now that you are aware of everything in a theoretical sense, additional safeguards have been introduced to ensure that only authorized individuals can see or edit the date.
Read to get a quick overview of the checklist: The Ultimate HIPAA Compliance Checklist For Healthcare Software Developers – TechVariable
Important procedures for creating an AWS infrastructure that complies with HIPAA
Making use of VPCs (Virtual Private Clouds)
VPCs can come in handy when creating a HIPAA-compliant infrastructure on AWS. A VPC enables the development of a logically separate region within the AWS cloud. By doing so, resources can be launched in any specified virtual network. Now, security groups and network ACLs that govern inbound and outbound traffic can be used to restrict access to PHI.
VPCs are logically separate areas of the AWS Cloud that have their own networking configurations. Scoping networking, rights, and data governance for various parts of your application is made simple by this.
Using IAM ( Identity and Access Management)
This enables resource-level controlled access to PHI. IAM policies provide users and programmes access to particular actions and resources. IAM also makes it possible to employ ‘roles’ to grant momentary access to resources, reducing the amount of long-term access keys in use.
PHI is protected both in transit and at rest thanks to encryption. Encryption keys are generated and managed by the AWS Key Management Service (KMS). AWS also provides a variety of encryption solutions, including server-side, client-side, and hardware security models (HSMs).
Using Multi-factor Authentication (MFA)
MFAs are an essential security technique that protects PHI by giving privileged access an additional degree of security. MFA alternatives from AWS include virtual MFA apps and hardware MFA gadgets.
Data Recovering
To ensure that important data is not lost in the event of major calamities, you must regularly backup your data. Data backup can be accomplished using a number of AWS products, including Amazon S3, Amazon RDS, and AWS Storage Gateway.
Monitoring, Reviewing, and Auditing
To preserve compliance with HIPAA, routine review and monitoring are essential. AWS offers a number of tools that track infrastructure and spot compliance and security flaws, including AWS CloudTrail, Amazon CloudWatch, AWS Config, and AWS Security Hub.
Additional Security and Response Plan
AWS collaborates with outside security companies like Trend Micro, McAfee, and Symantec to add further layers of security. In the event of a security breach, you must have a prepared reaction strategy. Any threat should be able to be found, contained, and reported to the appropriate authorities.
Appropriate Training for Development Team
Educating the project developers on the value of PHI protection and giving them the information and resources necessary to do so. They must be aware of the most recent laws and recommended procedures.
The AWS Compliance website, among other resources provided by AWS, can be utilized to keep up with the most recent legal developments.
Hiring Additional Hands
Working with a seasoned compliance expert is essential because they can guide the development team through the HIPAA compliance difficulties and make sure that the infrastructure is configured and maintained in accordance with the most recent rules.
To make sure the infrastructure is HIPPA compliant, working with skilled security experts and carrying out frequent risk assessments are crucial.
By following these best practices and working with experienced security professionals, healthcare organizations can build a secure and compliant infrastructure on AWS.
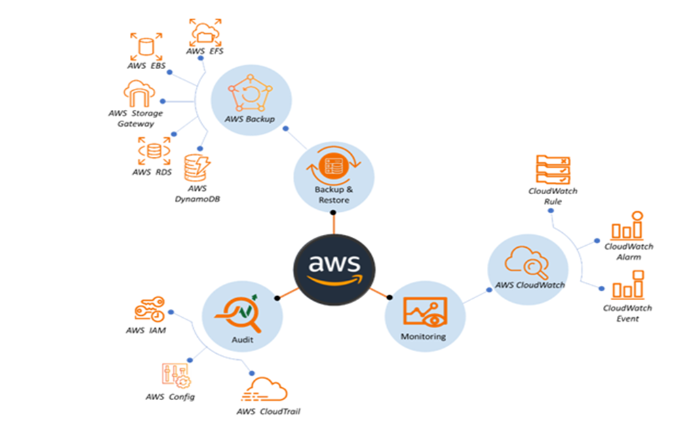
Various resources to audit, backup, and monitor infrastructure to maintain HIPAA compliance (Source: AWS)
Building the HIPAA Compliant AWS Architecture

To assist businesses in designing AWS cloud services around best security and compliance practices, AWS offers a cloud reference architecture or an AWS HIPAA Quickstart.
Further the architecture can be understood by the following –
In the VPC for management:
- A gateway to the internet that acts as a highly accessible, central point of exit for internet traffic.
- Private subnet resources can access the internet from public subnets thanks to controlled network address translation (NAT) gateways.
- Private subnets to implement your infrastructure and security measures.
- Auditing flow logging.
In the VPC:
- In the development VPC, private subnets are used to deploy development workloads, and flow logs are used for auditing. This helps to ensure that development resources are isolated from production and management resources and that all network traffic is logged for auditing purposes.
- In the management VPC, a gateway serves as a central point for internet traffic. Public subnets manage network address translation (NAT) gateways to allow internet access for private subnets resources. This will enable resources in the private subnets to access the internet while maintaining a high-security level. Additionally, private subnets are used to deploy security and infrastructure controls, and flow logs are used for auditing, which helps one to have better network traffic visibility.
- In the production VPC, private subnets are used to deploy production workloads, and flow logs are used for auditing. This helps to ensure that production workloads are isolated from development and management resources and that all network traffic is logged for auditing purposes.
AWS Transit Gateway enables customer connectivity and VPC-to-VPC communication.
For audit and logging controls:
- For metric monitoring and threshold alarms, use Amazon CloudWatch. Flow logs are delivered to an S3 bucket by this service.
- HIPAA compliance standards are mapped to specific AWS configuration items by AWS Config. Flow logs are delivered to an S3 bucket by this service.
- AWS CloudTrail for logging AWS access. Flow logs are delivered to an S3 bucket by this service.
For connecting with customers:
To connect with AWS Transit Gateway, use AWS Site-to-Site VPN or AWS Direct Connect.
For alerting and access control:
- Email alerts from alarms can be sent using Amazon Simple Notification Service (Amazon SNS).
- Access authorization and control are provided by AWS Identity and Access Management (IAM).
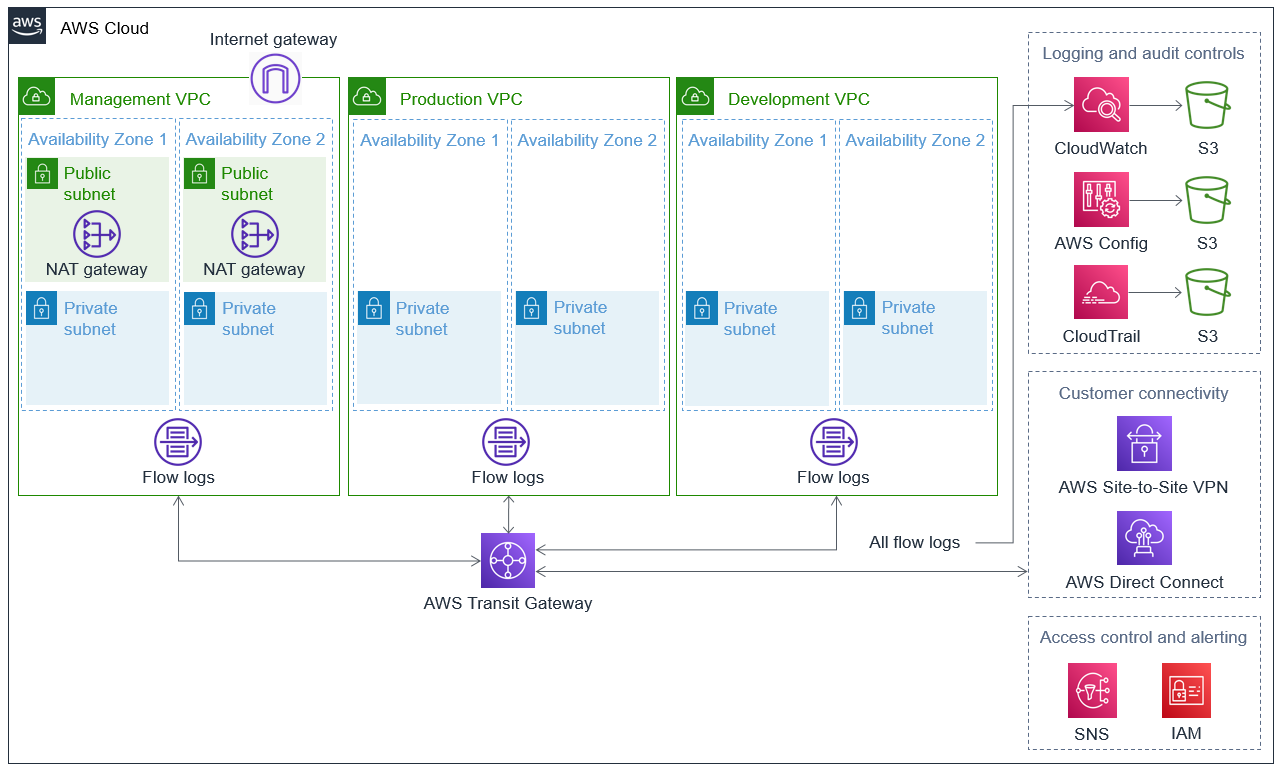
Basic Architectural Diagram (Source: AWS)
Way Forward
Every day, more healthcare providers choose AWS HIPAA-eligible services to ensure a high level of security for their services. AWS has shown that its services adhere to the HIPAA regulations and guarantees that ePHI can be processed and stored without any problems. Without a question, AWS makes it easier to create a reliable and consistent cloud environment. However, while developing a medical solution on AWS, healthcare organizations must have faith in their ability to appropriately configure AWS services to achieve all required security precautions. And you should use the aforementioned recommended practices in order to achieve AWS HIPAA compliance and a high level of security.
